Description
PHYLAWS stands for:
PHYsical LAyer Wireless Security
The following key topics are addressed:
- Enhancement of privacy at the radio interface of wireless networks
- Physical Layer Security (Physec) and Secrecy Coding
- Design of Trustworthy Wave Forms and Radio Access Protocols
- Realistic Test cases: WiFi (experiments) and LTE (simulation)
Motivations and intentions: The domination of Wireless Communications (as universal way to access information for nearly every human around the world) now presents a major risk to society, because of widely recognized security leaks in the current wireless radio access technologies. Basically, the security today relies on bit-level cryptographic techniques and associated protocols at various levels of the data processing stack. These solutions have drawbacks, which are currently major retarders to the progress of the digital society: standardized protections within public wireless networks are not secure enough, and many of their weaknesses are well known; even if enhanced ciphering and authentication protocols exist, they occur strong constraints and high additional costs for the users of public networks; etc.
New security approaches are issued from information theory fundamentals and focus on the secrecy capacity of the propagation channel. PHYLAWS will investigate them for handsets and communications nodes that operate at the radio interface. On the other side, R&D laboratories and industrials dealing with secured radio-networks have specific experience and practical means in order to design secure-improved terminal architectures, wave forms and radio access protocols, and to build relevant embedded modules. PHYLAWS elaborates on these wide knowledge bases in order to enhance the privacy of wireless public radio networks in an affordable, flexible, efficient and measurable manner, by focusing on four key items:
- Identify the most promising security techniques operating at the physical layer level or exploiting the physical characteristics of the transmitted signals.
- Identify the existing, upcoming of future systems, where these techniques might be implemented, without or with updates to the standards. Develop the suitable algorithms where necessary.
- Carry out theoretical, simulation based and experimental performance evaluation of these techniques, taking into account realistic use conditions, radio-electrical environments and propagation parameters. Demonstrate the capabilities of a selection of techniques in enhancing the information protection and the subscriber confidentiality.
- Demonstrate the capabilities of the selected techniques in reducing the redundancy of radio-communication signals, in enhancing the spectrum usage and the energy efficiency.
The impact will be societal (more confidence, more privacy) and industrial (supporting European industry in developing and commercializing such solutions). PHYLAWS is thus expected to sustain academic research and industrial development, to strongly impact standardization, to facilitate the penetration of wireless technologies in the personal and professional sphere, and to deeply contribute to trustworthy ICT in the following years.
The consultation services for wireless physical layer security cover:
- Secure advanced spatial diversity techniques (secure cooperative communications, secure two-way cooperative communications and secure MIMO communications, secure cognitive radio systems)
- Secure resource allocation (secure optimization, secure cross-layer optimization and game theory techniques)
- Multi-user information theoretical security (coordinated design and distributed design)
- Cross-layer designs for security
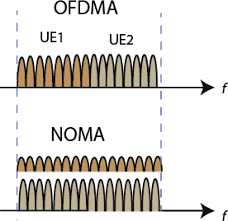
- Security for HetNets, massive MIMO, and mm-wave transmission
- Security and privacy in the Internet of Things
- Security for uRLLC and mMTC applications
- Trust, security and privacy in e-systems & social networking
- Trust, security and privacy in cloud computing
- Performance of practical testbeds for PLS